Zero Days might be scary but older known vulnerabilities are much more frightening – Techmonitor.ai
Published on: 2025-11-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Strategic Analysis of Cyber Vulnerabilities
1. BLUF (Bottom Line Up Front)
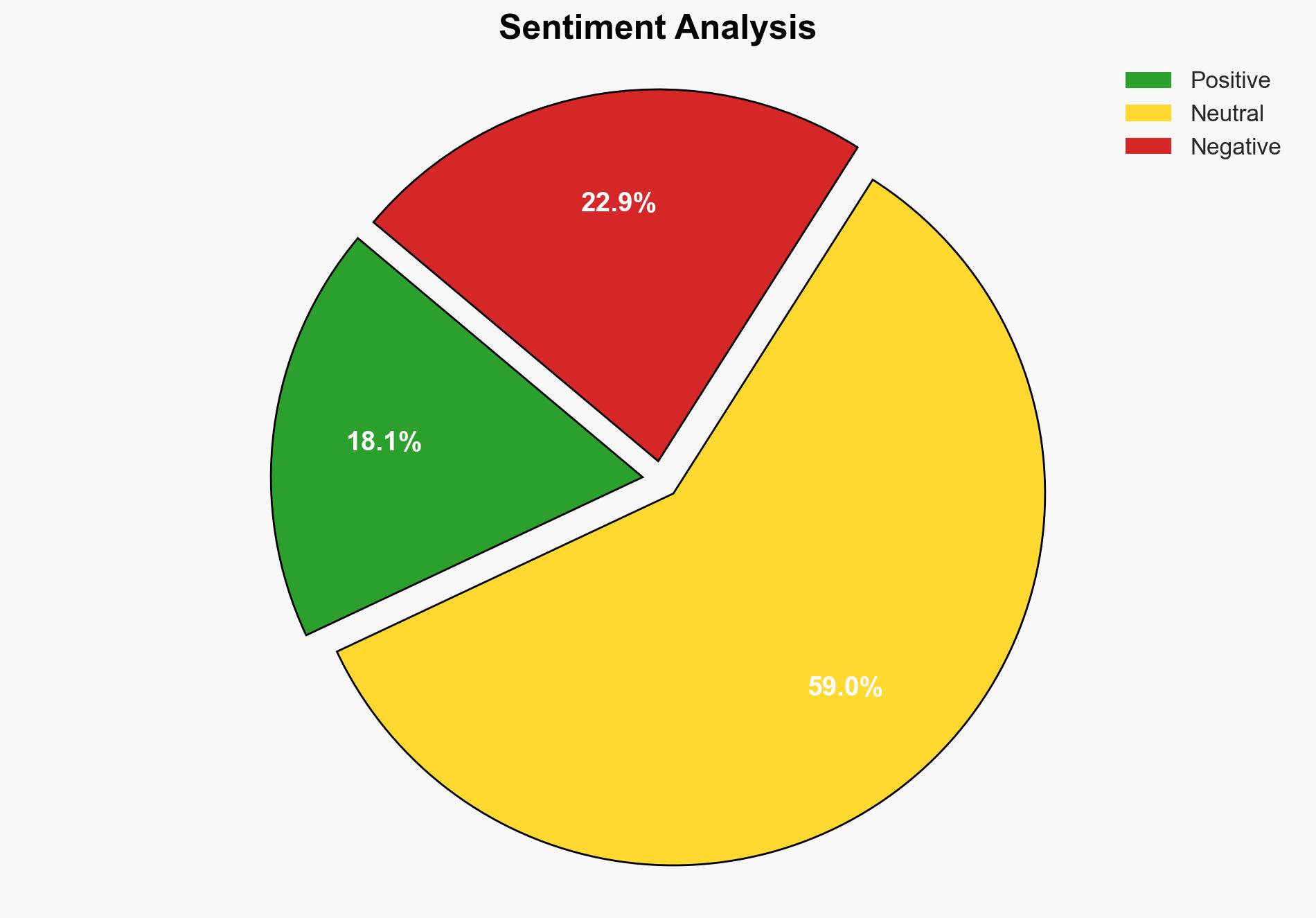
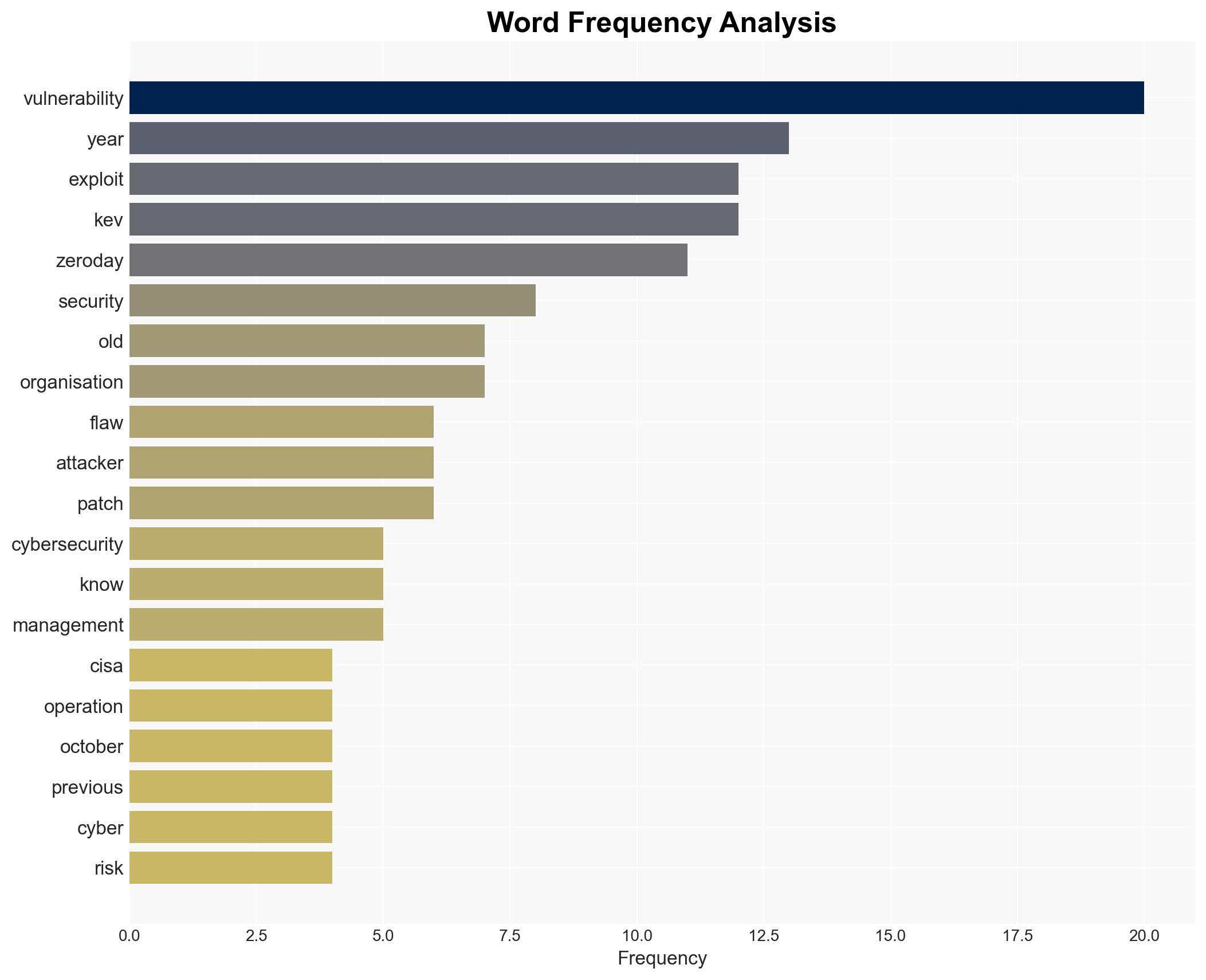
The most supported hypothesis is that older, known vulnerabilities pose a greater threat than zero-day exploits due to their widespread presence and ease of exploitation. This assessment is made with a high confidence level. Organizations should prioritize patching known vulnerabilities as outlined in the CISA KEV catalogue to mitigate risks effectively.
2. Competing Hypotheses
Hypothesis 1: Older, known vulnerabilities are a greater threat than zero-day exploits because they are easier to exploit and more prevalent in unpatched systems.
Hypothesis 2: Zero-day exploits pose a greater threat due to their unknown nature and potential for high-impact attacks before patches are available.
Assessment: Hypothesis 1 is more likely as it aligns with the observed trend of attackers favoring older vulnerabilities for their reliability and lower cost of exploitation. The CISA KEV catalogue’s focus on known vulnerabilities further supports this hypothesis.
3. Key Assumptions and Red Flags
Assumptions: Organizations have not adequately patched known vulnerabilities. Cybercriminals prioritize ease and cost-effectiveness in their attack strategies.
Red Flags: Over-reliance on the CISA KEV catalogue without considering emerging threats. Potential bias towards underestimating the impact of sophisticated zero-day attacks.
4. Implications and Strategic Risks
Failure to address known vulnerabilities could lead to widespread cyber incidents, affecting critical infrastructure and economic stability. Political tensions may rise if state actors exploit these vulnerabilities, leading to potential escalation in cyber warfare. Informational risks include reputational damage and loss of consumer trust.
5. Recommendations and Outlook
- Prioritize patching known vulnerabilities as per the CISA KEV catalogue.
- Conduct regular cyber simulations to test and improve vulnerability management processes.
- Balance security measures with operational uptime to ensure critical systems remain functional.
- Best-case scenario: Organizations effectively manage vulnerabilities, reducing the risk of major breaches.
- Worst-case scenario: A major attack exploiting known vulnerabilities causes significant disruption and economic loss.
- Most-likely scenario: Continued exploitation of known vulnerabilities with sporadic high-profile incidents.
6. Key Individuals and Entities
Ben McCarthy, Lead Cybersecurity Engineer at Immersive Labs, provides insights into the importance of addressing known vulnerabilities.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us