China-linked Silk Typhoon APT targets North America – Securityaffairs.com
Published on: 2025-08-23
Intelligence Report: China-linked Silk Typhoon APT targets North America – Securityaffairs.com
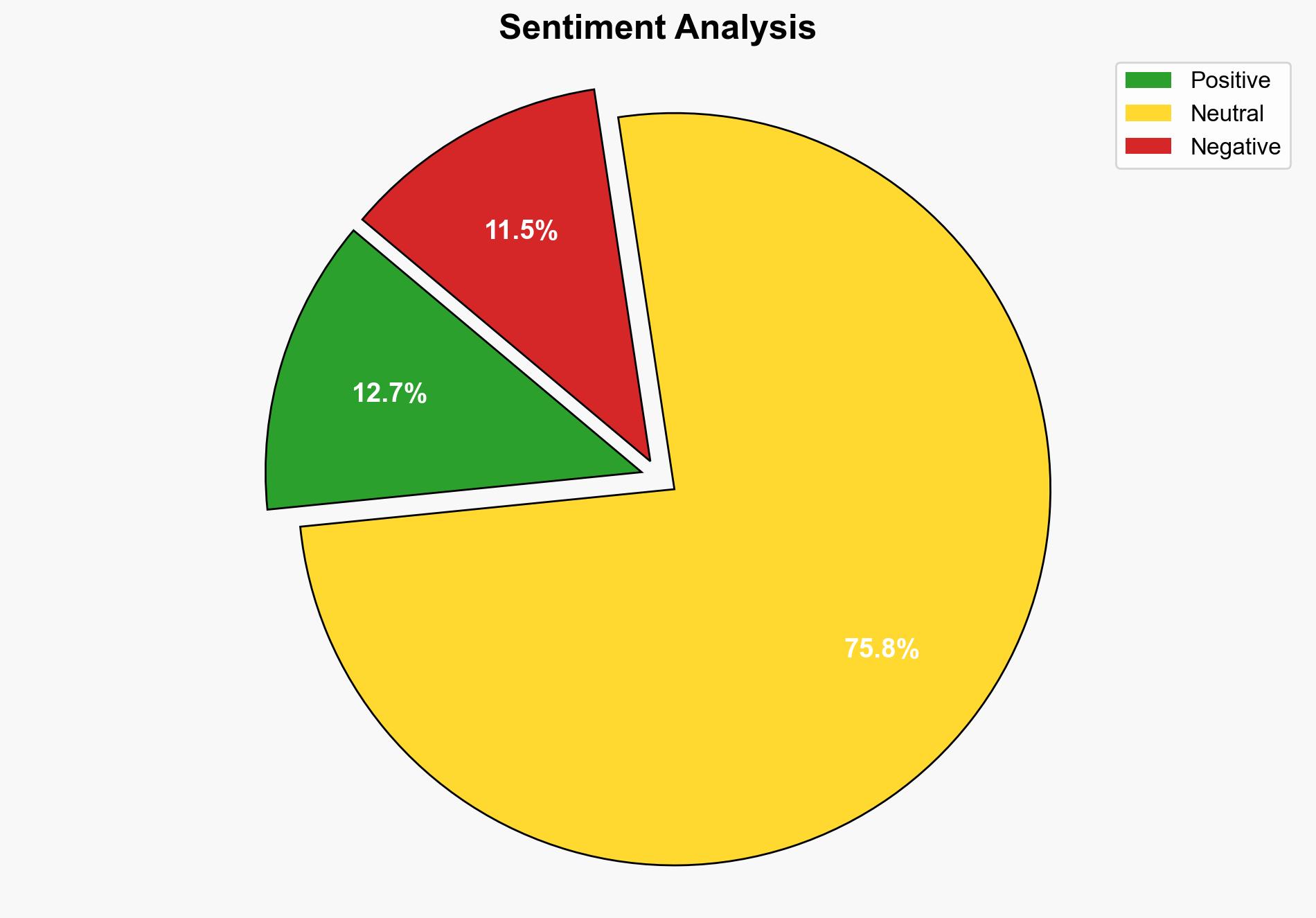
1. BLUF (Bottom Line Up Front)
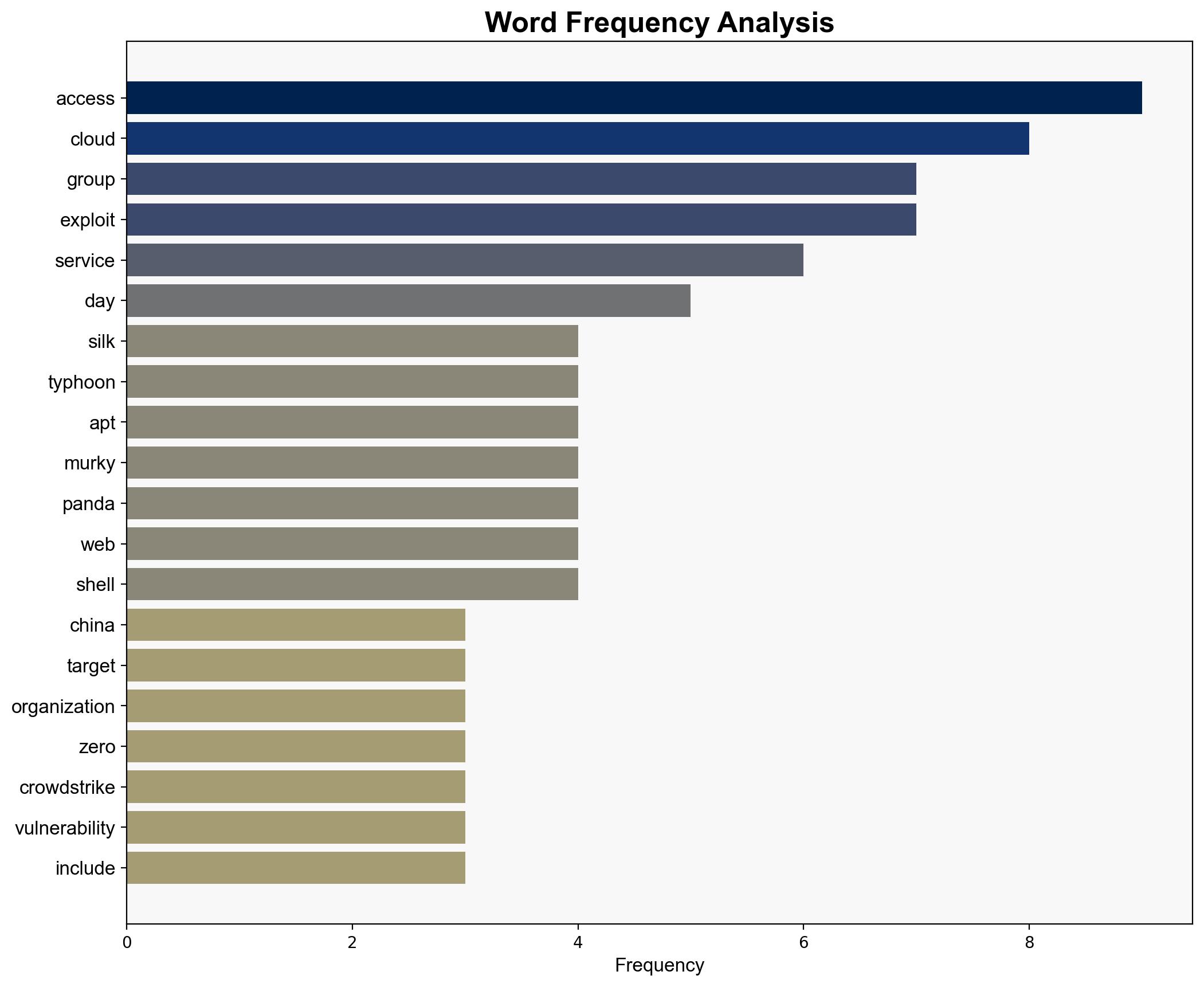
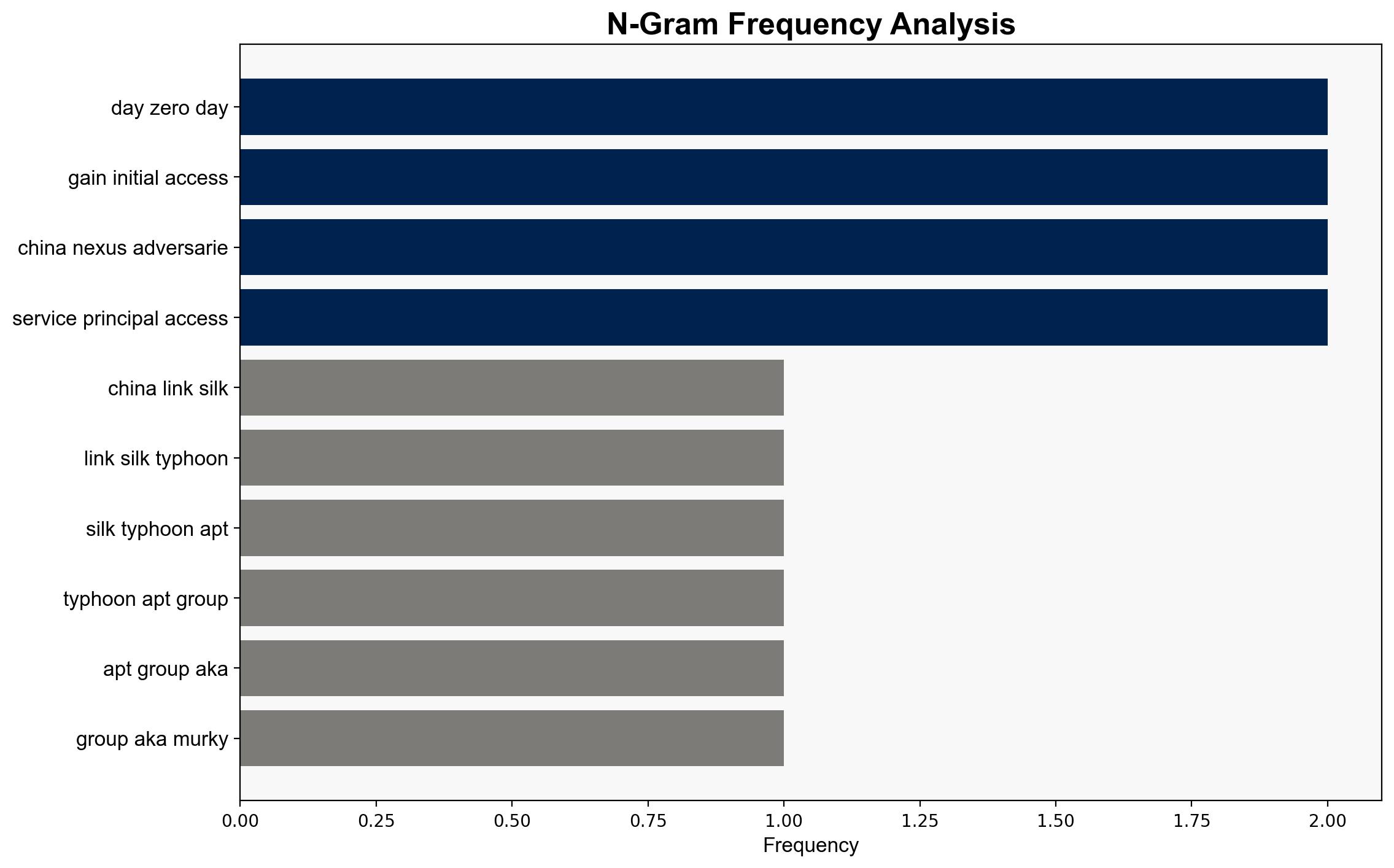
The Silk Typhoon APT group, linked to China, is actively exploiting vulnerabilities in North American organizations across multiple sectors, including technology, healthcare, and government. The most supported hypothesis is that Silk Typhoon is conducting a coordinated cyber-espionage campaign to gather intelligence and disrupt critical infrastructure. Confidence in this assessment is high. Recommended actions include enhancing cybersecurity measures, particularly in cloud environments, and increasing monitoring of known vulnerabilities.
2. Competing Hypotheses
Hypothesis 1: Silk Typhoon is engaged in a state-sponsored cyber-espionage campaign aimed at gathering intelligence and potentially disrupting critical infrastructure in North America. This hypothesis is supported by the group’s sophisticated techniques, such as exploiting zero-day vulnerabilities and leveraging cloud environments for persistence and data exfiltration.
Hypothesis 2: Silk Typhoon’s activities are primarily financially motivated, targeting sectors that can provide lucrative data for resale or ransom. This hypothesis considers the possibility of financial gain through data theft and extortion, although it is less supported given the group’s focus on intelligence collection and cloud-based tactics.
3. Key Assumptions and Red Flags
Assumptions include the belief that Silk Typhoon is state-sponsored due to its advanced capabilities and strategic targeting. A potential red flag is the reliance on open-source reporting, which may lack complete accuracy or context. Additionally, the assumption that all activities are centrally coordinated could overlook the possibility of independent actors within the group.
4. Implications and Strategic Risks
The activities of Silk Typhoon pose significant risks to national security, economic stability, and public trust in digital infrastructure. The exploitation of cloud environments highlights vulnerabilities in trusted relationships and could lead to widespread data breaches. Geopolitically, these actions may escalate tensions between China and North America, potentially leading to retaliatory cyber operations.
5. Recommendations and Outlook
- Enhance cybersecurity protocols, focusing on cloud security and zero-day vulnerability management.
- Increase collaboration between government and private sectors to share threat intelligence and best practices.
- Scenario-based projections:
- Best Case: Improved defenses lead to reduced impact of Silk Typhoon’s activities.
- Worst Case: Successful attacks result in significant data breaches and infrastructure disruptions.
- Most Likely: Continued attempts by Silk Typhoon with varying degrees of success, necessitating ongoing vigilance.
6. Key Individuals and Entities
The report does not provide specific names of individuals involved in Silk Typhoon. Key entities include CrowdStrike, Microsoft, and various North American sectors targeted by the group.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus