Millions of sites at risk from Imunify360 critical flaw exploit – Securityaffairs.com
Published on: 2025-11-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Millions of sites at risk from Imunify360 critical flaw exploit – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
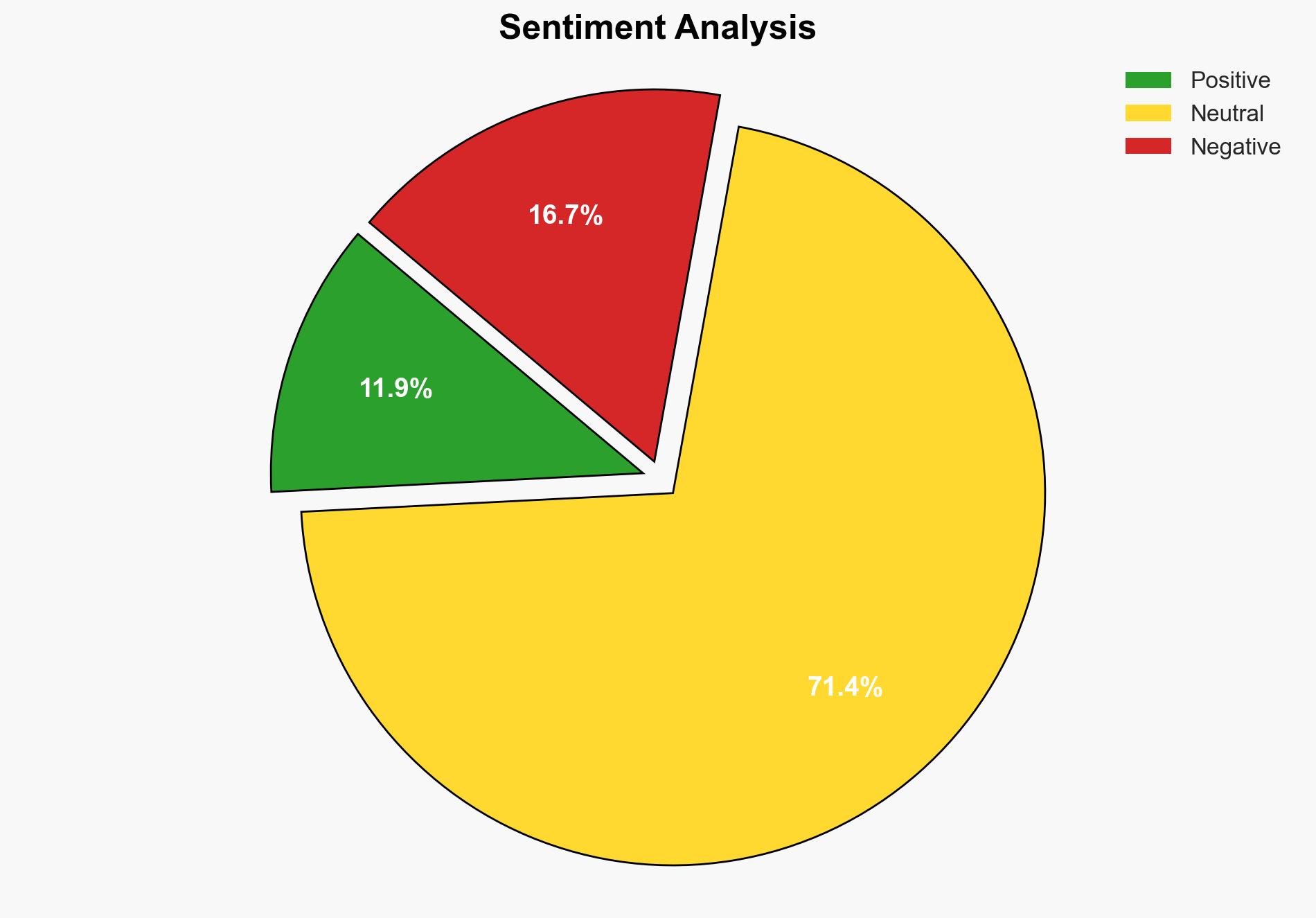
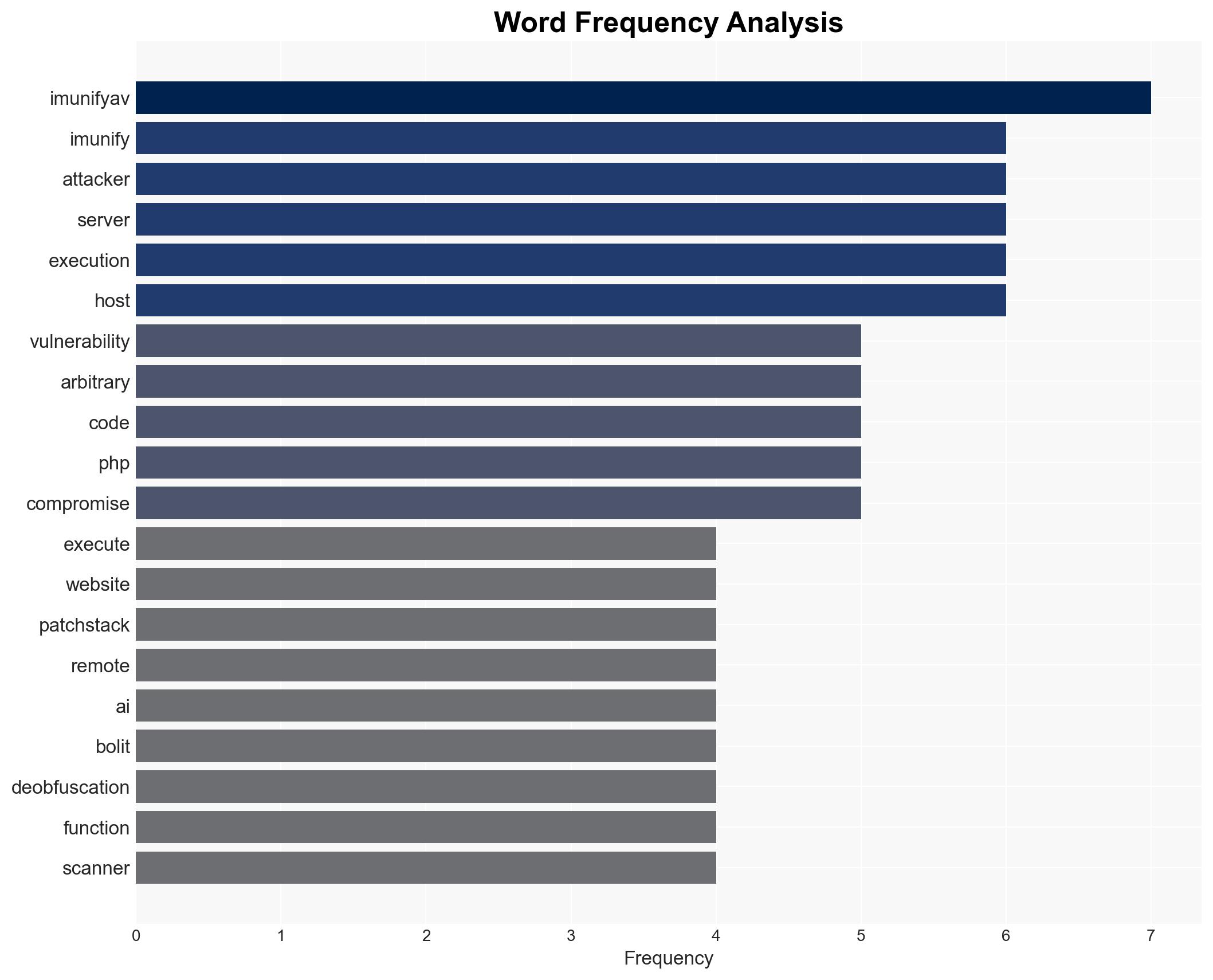
The most supported hypothesis is that the Imunify360 vulnerability presents a significant risk of widespread website compromise due to its potential for remote code execution. The confidence level is moderate due to the lack of evidence on active exploitation in the wild. Immediate patching and enhanced monitoring are recommended to mitigate risks.
2. Competing Hypotheses
Hypothesis 1: The Imunify360 vulnerability is being actively exploited by attackers, leading to widespread compromises of websites.
Hypothesis 2: The vulnerability is not yet being widely exploited, but the potential for exploitation remains high due to the public availability of technical details and proof of concept (PoC).
Hypothesis 2 is more likely given the current lack of evidence of active exploitation. However, the public disclosure of the vulnerability and PoC increases the risk of future exploitation.
3. Key Assumptions and Red Flags
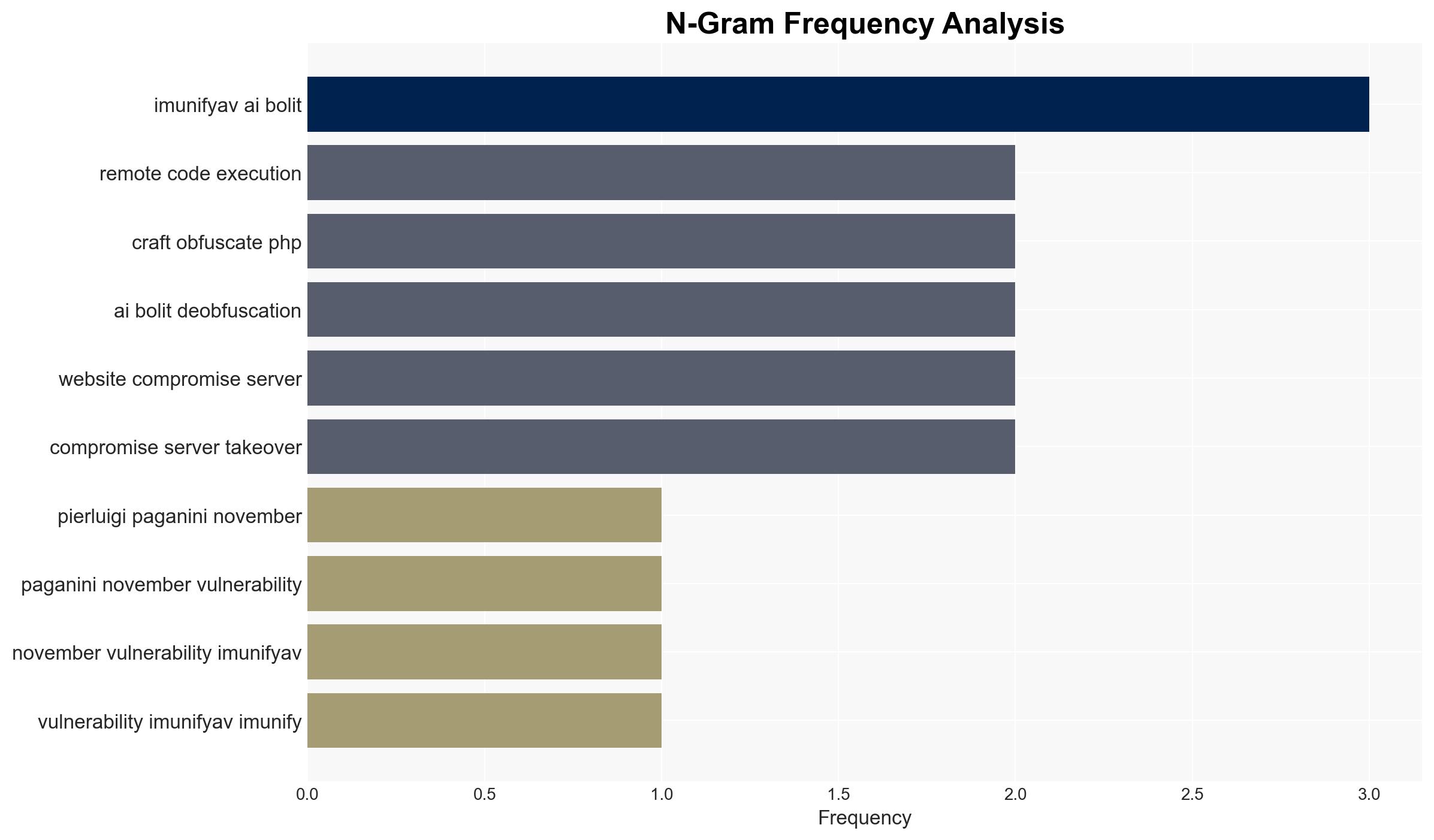
Assumptions: It is assumed that the vulnerability affects all versions of ImunifyAV prior to the patch and that patching will effectively mitigate the risk. It is also assumed that the vulnerability requires specific conditions to be exploited, such as active deobfuscation analysis.
Red Flags: The rapid release of technical details and PoC could accelerate exploitation. The complexity of the vulnerability might lead to underestimation of its impact by some organizations.
4. Implications and Strategic Risks
The vulnerability poses a risk of cascading cyber threats, including data breaches, defacement, and service disruption. If exploited, it could lead to significant economic impacts for affected businesses and reputational damage. Politically, exploitation by state actors could escalate tensions if used for espionage or sabotage.
5. Recommendations and Outlook
- Immediate action is required to patch affected systems and verify the integrity of websites.
- Enhance monitoring for signs of exploitation and anomalous activity.
- Best-case scenario: Rapid patching prevents widespread exploitation.
- Worst-case scenario: Delayed response leads to significant compromise and economic loss.
- Most-likely scenario: Limited exploitation occurs, but swift action mitigates major impacts.
6. Key Individuals and Entities
Pierluigi Paganini (Author), Patchstack (Cybersecurity firm), CloudLinux (Developer of Imunify360)
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·